H0neyTr4p

GitHub: https://github.com/pbssubhash/h0neytr4p
Presented in BlackHat Arsenal Europe '22
Built by Red teamers with 😻 for our Blue Team friends. Authors:
Rule Contributors:
What is h0neytr4p?
Honeytrap (a.k.a h0neytr4p) is an easy to configure, deploy honeypot for protecting against web recon and exploiting.
TLDR; This is how h0neytr4p traps a hypothetical attacker running nuclei!
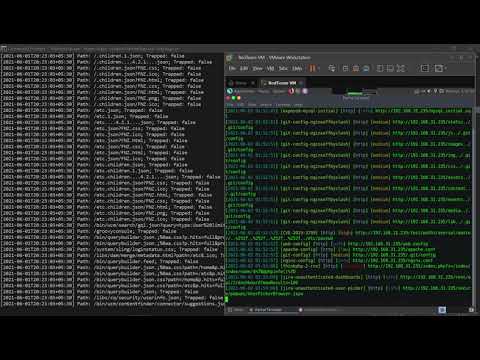
How does it work?
Blue teams can create trap for each vulnerability or exploit or recon technique and place it in the /traps folder and restart h0neytr4p. This will automatically reload the configuration and start the h0neytr4p.
What does it protect against?
h0neytr4p was primarly built to remove the pain of creating a vulnerable application for publicly facing honeypots. While there's no denying the fact that creating an end to end vulnerable application might have it's own advantages, we need something flexible, agile framework for trapping the notorious bad guys. Some of the common use-cases are:
Let's say you received an advisory that some XXX group is targetting a web RCE 1day and you want to detect the exploitation or recon attempts, you are at the right place.
You want to know who's scanning your external attack surface using the new cutting edge tools like nuclei or nmap? this tool got it covered.
How to deploy it?
The tool was build on top of Golang which means it can be easily compiled to your server/machine platform and architecture.
To Build from source (if you don't trust us):
Run Binaries directly (for my lazy homies):
Coming soon.
How can I create a trap?
Head to Creating Traps. We attempted to simplify the process.
Frequently asked questions:
I have an issue. Something's not working.
Please open an issue at Issues. We'll try to respond as soon as possible.
I found a security issue or a potential vulnerability that could impact it's users?
Please report on GitHub.
I want a new feature that's not there. What to do?
Please open an issue at Issues. Consider opening a pull request :-)
TO-DO:
Enable HTTPS
Push more traps to prod
Nice wiki
Last updated